Monitor your AWS network traffic without disrupting your systems. AWS VPC Traffic Mirroring enables you to duplicate and analyze network packets directly from Elastic Network Interfaces (ENIs) or EC2 instances. This helps with tasks like security monitoring, troubleshooting, and traffic analysis.
Here’s a quick summary of how it works:
- Source: The network interface where traffic is copied.
- Target: The destination (e.g., EC2 instance or Network Load Balancer) where mirrored traffic is sent.
- Filter: Rules to specify which packets to mirror.
- Session: Configuration linking the source, target, and filter.
Key Benefits
- Identify security threats by analyzing packet-level data.
- Troubleshoot connectivity issues in real time.
- Optimize network performance without impacting production systems.
Setup Requirements:
- Nitro-based EC2 instances as sources.
- Proper IAM permissions and security group configurations.
- Targets within the same VPC or connected VPCs.
Quick Setup Steps:
- Create a Traffic Mirror Target.
- Define a Traffic Mirror Filter with rules for specific traffic.
- Establish a Traffic Mirror Session linking the source, target, and filter.
Pro Tips:
- Use filters to capture only necessary traffic.
- Place targets in the same Availability Zone as sources to reduce latency.
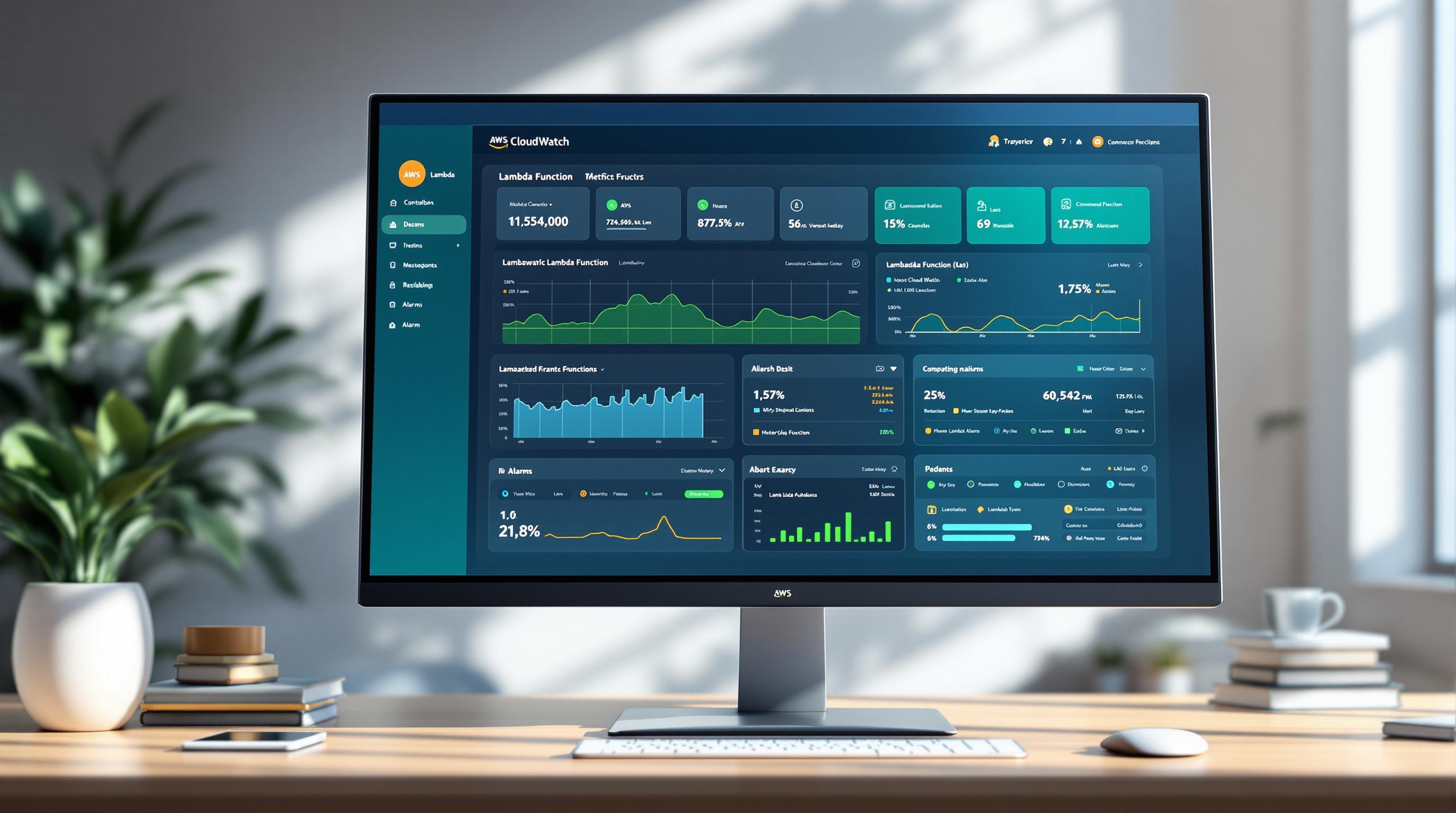
- Monitor CloudWatch metrics for performance and packet drops.
AWS VPC Traffic Mirroring gives you deep visibility into your network, helping you enhance security and troubleshoot efficiently. Follow these steps to get started!
AWS VPC Traffic Mirroring Basics
What is VPC Traffic Mirroring
AWS VPC Traffic Mirroring allows you to duplicate network traffic from EC2 instances for tasks like network monitoring, security checks, and packet-level analysis. It works by copying network packets from a source and sending those copies to a monitoring destination, while the original packets continue on their way.
Here’s how it works when an EC2 instance processes a client request:
- Captures the packet at the specified network interface.
- Makes a duplicate copy of the packet.
- Forwards the original packet as usual.
- Sends the duplicate packet to the monitoring destination.
Let’s break down the key components that make this process possible.
Main Traffic Mirroring Components
There are four main components involved in VPC Traffic Mirroring:
| Component | Description |
|---|---|
| Source | The network interface where traffic is captured. |
| Target | The destination that receives the mirrored traffic. |
| Filter | The set of rules that decide which packets should be mirrored. |
| Session | The configuration that connects the source, target, and filter. |
These components work together to let you capture and analyze network traffic without disrupting your applications' normal behavior.
How to Set Up Traffic Mirroring
This section explains how to configure traffic mirroring, building on the key components mentioned earlier.
Setup Requirements
Before you start, make sure the following are in place:
| Requirement | Description |
|---|---|
| Network Interface | An Elastic Network Interface (ENI) capable of supporting traffic mirroring |
| VPC Connectivity | The source and target must be within the same VPC or connected VPCs |
| IAM Permissions | Permissions to create and manage traffic mirror resources |
| Security Groups | Allow mirrored traffic between the source and target |
| Target Type | Either a Network Load Balancer or an EC2 instance to receive mirrored traffic |
Configuration Steps
Follow these steps to set up VPC Traffic Mirroring by configuring the target, filter, and session.
1. Create a Traffic Mirror Target
Go to the VPC Console and navigate to "Traffic Mirror Targets":
- Choose the target type (Network Load Balancer or ENI).
- Provide the network interface ID for the target.
2. Set Up Traffic Mirror Filter
- Define inbound and outbound rules.
- Specify protocols such as TCP, UDP, or ICMP.
- Set source and destination port ranges.
- Add IP address ranges to monitor.
3. Establish Traffic Mirror Session
- Pick the source network interface.
- Select the target you created earlier.
- Apply the filter rules and assign a session number (1-32766).
- Adjust packet size limits if required.
- Enable the session.
Once configured, the session becomes active immediately. Use AWS CloudWatch metrics to confirm that mirrored traffic is being captured.
sbb-itb-6210c22
Common Traffic Mirroring Uses
Traffic Mirroring expands on packet capture basics, providing practical applications for both operational needs and security measures.
Security Monitoring
Keep an eye on network traffic to detect threats, investigate packet-level intrusions, and maintain detailed logs for compliance purposes.
Network Troubleshooting
Identify connectivity and latency problems quickly with the insights provided by Traffic Mirroring.
Traffic Analysis
Examine traffic patterns between VPCs to pinpoint operational challenges. These tasks rely on the session and filter settings mentioned earlier.
Technical Limits and Tips
Service Limits
AWS VPC Traffic Mirroring comes with some restrictions and quotas you should be aware of:
Instance Support Restrictions
- Only Nitro-based EC2 instances can act as mirror sources.
- Network Load Balancers cannot function as mirror sources.
- The maximum packet size is 8,000 bytes; packets larger than this may get truncated.
Service Quotas
- Up to 500 mirror targets per region.
- A maximum of 1,000 mirror sessions per region.
- Support for 10,000 mirror filters per region.
- Each filter can have up to 3 rules.
Bandwidth Considerations
- Mirror sessions use network bandwidth from the source instances.
- Mirrored traffic counts toward the network bandwidth limits of the source instance.
- Target instances must handle the combined traffic from multiple sources effectively.
Implementation Tips
To work within these limits, consider the following strategies:
Fine-Tune Filters
- Design filters to capture only the traffic you need. This helps reduce unnecessary data and optimizes performance.
Choose the Right Target Instance
- Select target instances based on the expected traffic volume.
- Regularly monitor CPU and network usage on target instances. Use auto-scaling groups to manage fluctuating loads.
Enhance Security
- Use security groups to restrict access to mirror targets.
- Apply strict IAM policies to control who can manage Traffic Mirroring.
Boost Performance
- Place mirror targets in the same Availability Zone as the source instances to minimize latency.
- Dedicate specific targets for high-traffic sources to avoid overload.
- Keep an eye on CloudWatch metrics to detect issues like packet drops or increased latency.
Conclusion
AWS VPC Traffic Mirroring offers a way to monitor, detect threats, and troubleshoot your network without disrupting production workloads. With its filtering options and seamless integration within AWS, it helps teams analyze network traffic efficiently.
To get the most out of VPC Traffic Mirroring, keep these tips in mind:
- Allocate resources wisely based on service limits, place mirror targets close to sources for better performance, and implement strong security measures.
This tool equips engineers with the packet-level insights they need for effective network monitoring and security, all while staying within AWS service constraints.