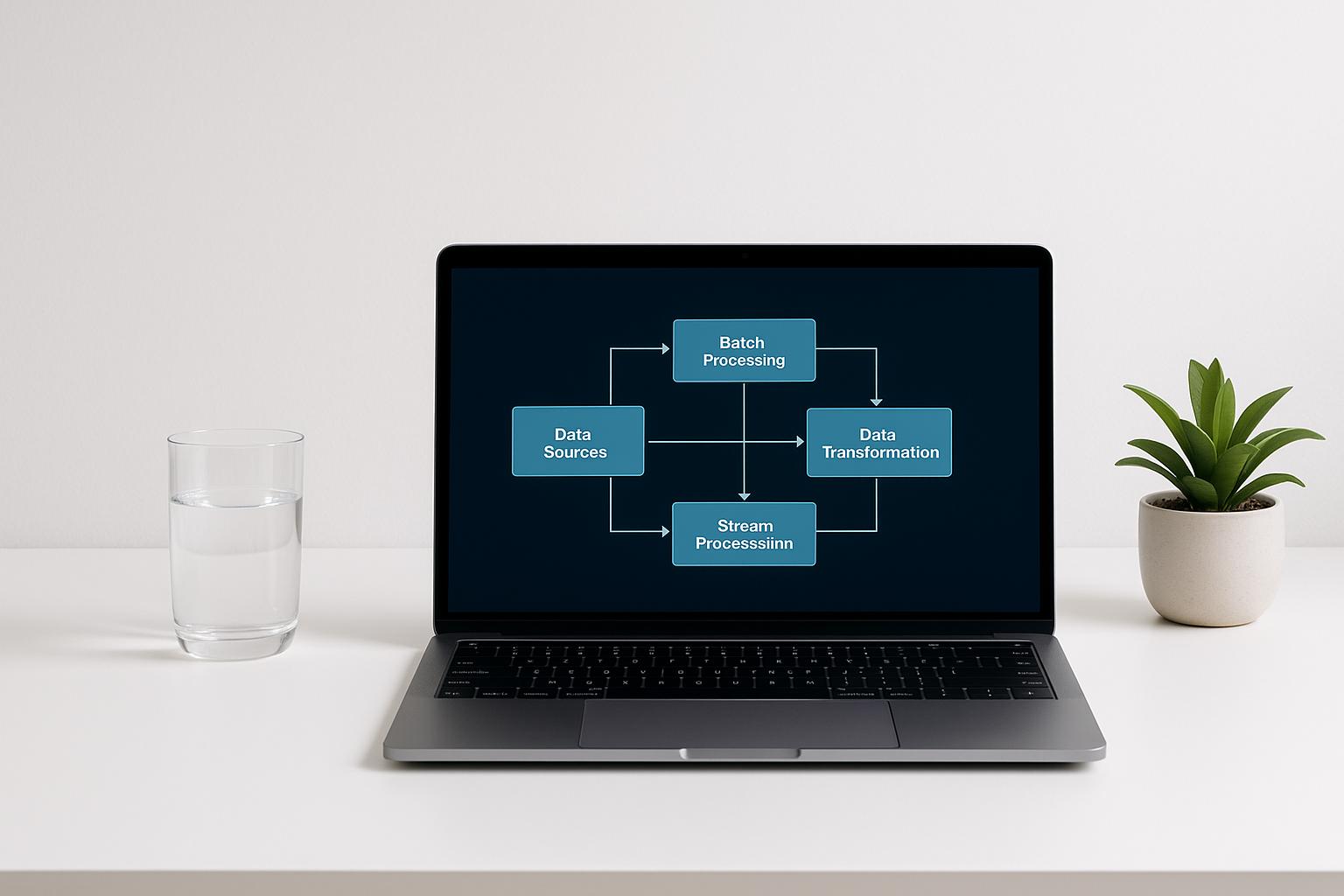
Need to track AWS activity but not sure which logs to use? Here's the quick answer:
- S3 Access Logs: Best for monitoring object-level actions in S3 buckets, like GET, PUT, and DELETE requests. Use them to analyze access patterns, troubleshoot errors, and track presigned URL activity.
- CloudTrail Logs: Ideal for tracking API-level activity across AWS services. Use them for security audits, compliance, and monitoring cross-service interactions.
Quick Comparison
| Feature | S3 Access Logs | CloudTrail Logs |
|---|---|---|
| Scope | Object-level (S3-specific) | API-level (all AWS services) |
| Details Captured | Basic (e.g., request time, IP, status code) | Detailed (e.g., API parameters, IAM user) |
| Best For | Access patterns, error detection | Security audits, compliance, multi-service tracking |
| Format | CSV-like | JSON |
| Delivery Time | Almost real-time | ~15 minutes delay |
Use Both for Comprehensive Monitoring
Combine S3 Access Logs and CloudTrail Logs to gain detailed insights into object-level operations and broader API activity across AWS services.
Key Tip: Focus logging on critical buckets or services to reduce costs and manage resources effectively.
Differences Between S3 Access Logs and CloudTrail
Understanding the differences between S3 Access Logs and CloudTrail can help you fine-tune your logging strategy.
Log Coverage
S3 Access Logs and CloudTrail focus on different aspects of monitoring. Here's a quick comparison:
| Operation Type | S3 Access Logs | CloudTrail |
|---|---|---|
| Object Access (GET, PUT, DELETE) | ✓ | Limited |
| Bucket Configuration Changes | Limited | ✓ |
| Cross-Service API Calls | ✗ | ✓ |
| IAM Identity Details | Basic | Detailed |
| Request Parameters | Basic | Detailed |
Log Output and Storage
S3 Access Logs:
- Delivered almost in real-time to a specified S3 bucket.
- Comes in a CSV-like format, making it easier to parse.
- Logs can be stored in the monitored bucket or a different one.
- Organized using a structured hierarchy (year/month/day).
CloudTrail Logs:
- Typically delivered with a delay of about 15 minutes.
- Uses JSON format, which includes metadata for deeper context.
- Requires a separate S3 bucket for log storage.
- Provides more detailed fields, including API context and security-related information.
Best Uses
S3 Access Logs:
- Ideal for tracking object-level access.
- Useful for identifying error patterns.
- Helps monitor activity related to presigned URLs.
CloudTrail Logs:
- Best suited for security monitoring.
- Tracks activity across multiple AWS services.
- Supports compliance and detailed security analysis.
For object-level tracking, S3 Access Logs are the way to go. Meanwhile, CloudTrail offers a broader view of API activity and is essential for security-focused tasks. Combining both can provide a more comprehensive monitoring solution. Next, we’ll look at specific scenarios where each logging type excels.
When to Use S3 Access Logs
S3 Access Logs are perfect for detailed, object-level monitoring, especially when it comes to security, troubleshooting, and compliance needs.
Object Access Tracking
S3 Access Logs provide in-depth tracking of operations at the object level. They capture details like:
- The full ARN for external users
- The AWS account ID and IP address of the requester
- Exact timestamps of requests and how long they took to process
- The type of operation performed (e.g., GET, PUT, DELETE)
- Response status codes and any error codes
This level of granularity sets S3 Access Logs apart from CloudTrail, which focuses more on high-level API activities. For example, in environments with multiple accounts - like shared data lake buckets - S3 Access Logs can capture detailed identity information for cross-account users. In contrast, CloudTrail is limited to broader account-level details.
Error Pattern Detection
S3 Access Logs are also great for identifying error patterns caused by bucket misconfigurations. Here's how:
| Error Type | Details Captured | Use Case |
|---|---|---|
| HTTP Status Codes | 200, 403, 404, etc. | Differentiating successful and failed requests |
| Error Codes | NoSuchKey, AccessDenied | Pinpointing specific reasons for failures |
| Performance Metrics | Bytes sent/received, latency | Monitoring response times and performance |
By analyzing these logs, you can uncover issues like recurring 403 errors, which might suggest incorrect IAM permissions, or clusters of 404 errors, which could indicate attempts to access objects that don’t exist.
Presigned URL Monitoring
Another useful feature of S3 Access Logs is their ability to track presigned URL activity. They log:
- Information about the original requester
- The timestamps of access attempts
- Details about the requested resources
- Whether the access attempt succeeded or failed
This is particularly helpful for spotting potential security issues, such as unauthorized sharing of URLs, usage beyond their intended timeframes, or unusual access patterns.
S3 Access Logs are stored using standard S3 storage fees, making them a budget-friendly option for long-term monitoring. Their detailed tracking capabilities make them an excellent choice over CloudTrail in scenarios requiring object-level insights, as we’ll explore further in the next section.
When to Use CloudTrail Logs
CloudTrail keeps a close eye on API activity across AWS, making it a go-to tool for thorough security analysis. Its role in detecting, analyzing, and responding to security events is indispensable.
Security Monitoring
One of CloudTrail's strengths is its ability to track IAM activities and API calls. Here's a quick breakdown of what it logs:
| Activity Type | Details Captured | Security Purpose |
|---|---|---|
| IAM Changes | Policy updates, role creation or deletion | Spot unauthorized changes to permissions |
| API Calls | Caller identity, timestamps, and parameters | Detect unusual access patterns |
| Console Actions | Logins, configuration changes | Keep tabs on administrative actions |
This comprehensive monitoring extends into CloudTrail's ability to observe how different AWS services interact.
Multi-Service Tracking
What sets CloudTrail apart is its capability to track interactions between AWS services. It captures:
- API calls between services like S3 and others
- Data transfers, such as S3 triggering a Lambda function
- Changes in service configurations
This interconnected view is invaluable when troubleshooting complex workflows. For instance, imagine an S3 bucket triggering a Lambda function that updates DynamoDB. CloudTrail logs the entire sequence, making it easier to pinpoint issues in your application’s architecture.
Compliance and Security Analysis
CloudTrail also shines when it comes to meeting compliance standards and conducting security investigations. Here’s how:
1. Immutable Log Files
CloudTrail logs can be set up with write-once-read-many (WORM) protection. This ensures logs remain untampered - critical for compliance needs.
2. Integration with Security Tools
It works seamlessly with AWS GuardDuty and Security Hub to automate threat detection.
3. Detailed Audit Trail
CloudTrail provides a thorough record of:
- Who accessed AWS resources
- When the access happened
- What actions were taken
- The outcomes of those actions
This level of detail is especially valuable for industries with strict regulations, such as healthcare (handling PHI) or finance (meeting SOX compliance).
While it doesn’t capture object-level details, its ability to log cross-service activity and maintain secure, unalterable audit trails makes it an essential tool for maintaining security and meeting compliance requirements. If your focus is on monitoring inter-service activity and ensuring a robust security posture, CloudTrail is the way to go.
sbb-itb-6210c22
Selecting the Right Logging Method
When it comes to choosing the best logging method for your needs, it’s essential to weigh the specific use cases and operational goals discussed earlier. Here’s how to decide between S3 Access Logs and CloudTrail Logs - or even use both for a more comprehensive approach.
Selection Factors
The choice between S3 Access Logs and CloudTrail Logs largely depends on what you’re aiming to monitor. Here's a quick breakdown:
| Factor | S3 Access Logs | CloudTrail Logs |
|---|---|---|
| Primary Use Case | Tracks object-level operations to analyze access patterns and detect errors | Monitors API-level activity for security and multi-service event tracking |
Using Both Log Types
For a well-rounded monitoring strategy, consider combining both logging methods. This layered approach offers:
- Granular Access Details: S3 Access Logs provide detailed insights into object-level operations, such as who accessed what and when.
- Broader Monitoring: CloudTrail Logs capture administrative actions, resource changes, and cross-service interactions.
By leveraging both, you gain a more complete view of your system's activity, enhancing both operational efficiency and security.
Resource Impact
While logging is critical, it’s important to manage the resource demands it creates. Here are some tips to minimize overhead:
- Enable Selective Logging: Focus detailed logging on critical or sensitive buckets to reduce unnecessary data collection.
- Use Lifecycle Policies: Automatically archive or delete older logs to save storage space and keep your system tidy.
- Consolidate Logs: Aggregate logs from multiple buckets into a central location to simplify monitoring and reduce complexity.
Balancing your monitoring needs with resource consumption ensures that your logging strategy remains effective without overwhelming your infrastructure.
Conclusion
Decide between S3 Access Logs or CloudTrail logs based on what you need to monitor.
Summary
Here’s a quick rundown to help shape your logging strategy:
| Logging Type | Primary Purpose | Best For |
|---|---|---|
| S3 Access Logs | Object-level operations | Tracking data access patterns, errors, and presigned URLs |
| CloudTrail Logs | API-level activity | Security audits, multi-service tracking, and compliance |
| Combined Approach | Comprehensive monitoring | Organizations needing both object-level and API activity insights |
To refine your logging approach, consider these points:
- Object-Level Monitoring: Use S3 Access Logs for a closer look at specific object operations.
- Security and Compliance: Rely on CloudTrail logs for broader API activity tracking and meeting compliance goals.
FAQs
When should I use S3 Access Logs and CloudTrail Logs together for better security monitoring?
S3 Access Logs and CloudTrail Logs work hand in hand to give you a clearer picture of your AWS environment's security. S3 Access Logs focus on the nitty-gritty details of requests to your S3 buckets, like who made the request, what operation was performed, and when it happened. CloudTrail Logs, on the other hand, track API activity across your entire AWS account, covering S3 as well as other services.
When you combine these two types of logs, you get both a high-level overview of account activity and a detailed look at bucket-level access. For instance, CloudTrail can help you spot unauthorized API calls or unusual behavior across your account, while S3 Access Logs fill in the finer details about specific bucket interactions. Together, they provide a stronger foundation for identifying potential security issues and meeting auditing requirements.
What are the costs of using S3 Access Logs and CloudTrail Logs, and how can I optimize them?
Both S3 Access Logs and CloudTrail Logs can lead to extra charges, depending on how you set them up and use them. For S3 Access Logs, costs arise from storing and retrieving them in S3 buckets. Meanwhile, CloudTrail Logs can incur expenses for S3 storage and, optionally, for analysis using tools like CloudWatch Logs or Athena.
Here are some tips to keep these costs under control:
- Enable logging selectively: Activate logging only for specific buckets or events that truly need monitoring.
- Apply lifecycle policies: Set up S3 lifecycle rules to move logs to cheaper storage classes or delete them after a certain time.
- Consolidate logs: Combine logs into fewer buckets or regions to simplify management and reduce retrieval expenses.
A well-thought-out logging strategy can help you maintain the right level of visibility while keeping costs in check.
When should I use S3 Access Logs instead of CloudTrail Logs for compliance?
S3 Access Logs are perfect when you need detailed insights at the bucket level to understand access patterns and operations. These logs capture specifics like the requester’s IP address, the time of the request, and the actions performed. This level of detail makes them invaluable for monitoring bucket activity and addressing compliance requirements that call for visibility into data access.
CloudTrail Logs, however, focus on tracking API-level activity across your entire AWS account. They cover actions performed on S3 as well as other AWS services. If your compliance standards require a broader view of account activity or auditing changes at the API level, CloudTrail is the better fit.
For a more complete picture of your S3 usage and to meet regulatory requirements, combining both logs can be a smart solution.